전세계적인 클라우드 사용기업의 IT시스템 먹통 사고가 발생한 가운데 이를 해결하기 위해서는 백업 복원 또는 안전모드에서 ‘C-00000291*.sys’ 파일을 찾아 삭제를 해 임시 복구를 해야 하는 것으로 나타났다. #CrowdStrike #Azure #AWS
백업에서 복원 가능시 2024년 7월19일 04:09 UTC 이전부터 복원
전세계적인 클라우드 사용기업의 IT시스템 먹통 사고가 발생한 가운데 이를 해결하기 위해서는 백업 복원 또는 안전모드에서 ‘C-00000291*.sys’ 파일을 찾아 삭제를 해 임시 복구를 해야 하는 것으로 나타났다.
2024년 7월19일 04:09 UTC에 클라우드 플랫폼에서 CrowdStrike Falcon 에이전트를 사용하는 Windows 시스템이 응답 없음 또는 시작 실패가 발생하는 사고가 발생했다.
이에 전세계 항공, 쇼핑, 배송, 의료 사회 각 분야에서 시스템이 먹통이 되는 심각한 문제가 발생했다.
이러한 긴급 상황을 해결하기 위해 크라우드스트라이크가 긴급 복구 방안을 내놨다.
크라우드스트라이크에 따르면 우선 시스템 상황을 파악하는 것이 중요한데 증상에는 Falcon Sensor 영향을 받지 않은 Windows 호스트는 문제가 있는 채널 파일이 되돌려졌으므로 조치가 필요없다.
05:27 UTC 이후에 온라인 상태가 된 Windows 호스트도 영향을 받지 않는다.
이 문제는 Mac 또는 Linux 기반 호스트에 영향을 주지 않는다.
타임스탬프가 05:27 UTC 이상인 채널 파일 ‘C-00000291*.sys’는 되돌려진(양호한) 버전이다.
타임스탬프가 04:09 UTC인 채널 파일 ‘C-00000291*.sys’은 문제가 있는 버전이다.
참고로 CrowdStrike 디렉토리에 여러 개의 ‘C-00000291*.sys’ 파일이 있는 것은 정상이며, 폴더에 있는 파일 중 하나에 05:27 UTC 이상의 타임스탬프가 있는 한 활성 콘텐츠가 된다.
■ 개별 호스트에서의 해결 방법
문제가 된 시스템을 해결하기 위해서는 윈도우를 안전 모드 또는 윈도우 복구 환경으로 부팅한다.
WinRE/WinPE에서 OS 볼륨의 Windows\System32\drivers\CrowdStrike 디렉터리로 이동한다.
‘C-00000291*.sys’와 일치하는 파일을 찾아 삭제한다.
호스트를 정상적으로 부팅한다.
참고로 Bitlocker로 암호화된 호스트에는 복구 키가 필요할 수 있다.
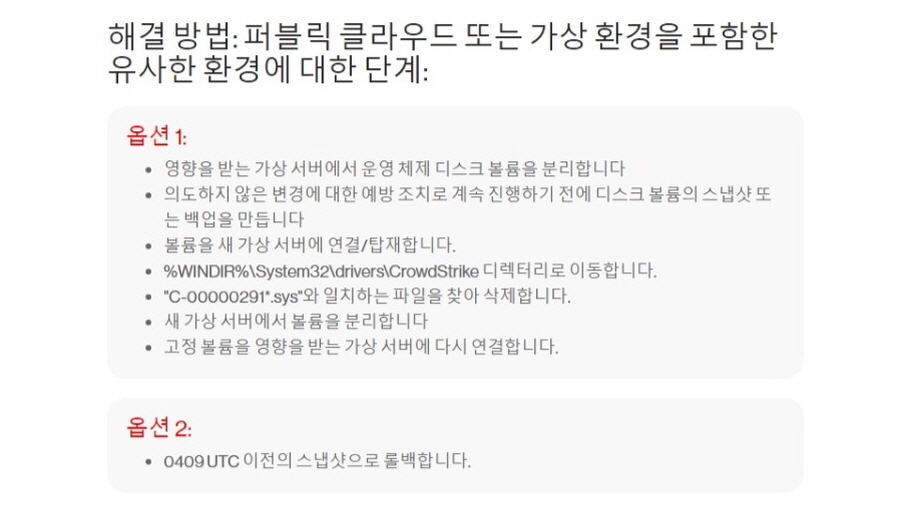
■ 퍼블릭 클라우드 또는 가상환경에서의 해결 방법
우선 영향을 받는 가상서버에서 운영체제 디스크 볼륨을 분리한다.
의도하지 않은 변경에 대한 예방조치로 계속 진행하기 전에 디스크 볼륨의 스냅샷 또는 백업을 만든다.
볼륨을 새 가상 서버에 연결, 탑재한다.
%WINDIR%\System32\drivers\CrowdStrike 디렉터리로 이동한다.
‘C-00000291*.sys’와 일치하는 파일을 찾아 삭제한다.
새 가상 서버에서 볼륨을 분리한다.
고정 볼륨을 영향을 받는 가상 서버에 다시 연결한다.
위 방법 이외의 두 번째 방법으로는 04:09 UTC 이전의 스냅샷으로 롤백한다.
자세한 정보는 크라우드스트라이크 홈페이지, MS Azure 홈페이지, AWS 홈페이지 등에서 확인할 수 있다.